· Jane Iamias · vendors due diligence · 18 min read
A Practical Guide to Vendors Due Diligence
Master vendors due diligence with our practical guide. Learn how to build a response kit, navigate scrutiny, and turn compliance into a sales advantage.

Vendor due diligence is the process of putting potential third-party suppliers under the microscope. It’s all about protecting your business from the financial, operational, and reputational fallout that can happen when a partner relationship goes sour. What used to be a tick-box exercise has now become a crucial, non-negotiable part of the B2B sales cycle, largely thanks to growing cyber risks and ever-tighter regulations.
Why Vendor Due Diligence Is No Longer Optional
The business world has changed. A partner’s flashy product features now often take a backseat to the trust and security they can actually guarantee. A few years ago, due diligence might have been a quick, informal check-up. Today, it’s a deep, ongoing examination of a vendor’s entire operational and security posture. This isn’t change for change’s sake; it’s a direct response to a market that is now painfully aware of risk.
We’ve all seen the headlines about high-profile data breaches that started with a compromised third party. These incidents have shown companies the brutal consequences of not vetting their partners properly. The infamous Target data breach in 2013, for example, began with credentials stolen from an HVAC vendor. It was a harsh lesson that any partner, no matter how small or seemingly insignificant, can be an entry point for an attack.

A Strategic Shift from Defence to Offence
Seeing vendor due diligence as just another defensive chore is a huge missed opportunity. The smartest businesses now use it as a proactive strategy to build trust and actually speed up the sales process.
For instance, in the UK private equity market, it’s becoming common for sellers to commission their own independent due diligence reports to share with potential buyers. This tactic, as explored in how VDD is shaping UK M&A transactions, helps to eliminate surprises and boost bidder confidence. It proves that being prepared gives you a serious competitive edge.
This evolution is all part of a wider move towards building stronger risk mitigation frameworks. To really get to grips with the core principles that make vendor due diligence so essential, it’s worth exploring the fundamentals of third-party risk management.
The simple truth is this: your customers aren’t just buying your product. They are buying into your entire ecosystem of security and operational resilience. A smooth, transparent due diligence process proves you’re a low-risk, high-value partner worth investing in.
The Impact of a Risk-Aware Market
Today’s buyers are more informed and cautious than ever before. They are held responsible for the security of their entire supply chain, which means they have to scrutinise every single vendor they bring on board.
This heightened scrutiny means you, as a vendor, must be ready to answer detailed questions about everything from your security protocols to your financial health. They’ll want to know about:
- Information Security: Your protocols for protecting data, including access controls, encryption, and incident response plans.
- Regulatory Compliance: Your adherence to standards like GDPR, SOC 2, and any other industry-specific regulations that apply.
- Financial Stability: Your ability to prove you’ll be a viable, stable partner for the long haul.
- Operational Resilience: Your business continuity and disaster recovery plans—what happens when things go wrong?
At the end of the day, robust vendor due diligence isn’t a barrier to sales. It’s a gateway to building stronger, more trusted partnerships that last.
Assembling Your Due Diligence Response Kit
Waiting for a due diligence questionnaire to land in your inbox before you start gathering documents is a recipe for disaster. The best vendors treat this as a proactive exercise, building a comprehensive response kit long before the first request ever arrives.
Think of this kit as your “single source of truth.” It’s a centralised, organised library of all the documents, policies, and evidence a potential customer could ever ask for. This preparation shifts the entire dynamic from a last-minute, panicked scramble to a calm, professional, and efficient process.
It’s not just about saving time, either. Presenting a well-organised set of documents right from the start shows maturity. It tells a potential customer that you take their security and compliance seriously, building crucial trust from day one.
Foundational Security and Compliance Documents
Let’s start with the absolute essentials. These are the core documents that form the bedrock of your security posture. If a prospect asks for anything, it will likely be something from this list. Without these, you’ll struggle to get past the first hurdle.
You’ll want to have these ready to go:
- Information Security Policy (ISP): This is your keystone. It’s the high-level document that outlines your organisation’s commitment and rules for protecting data.
- Compliance Certifications: If you’ve put in the hard work to get certified, show it off. Have your SOC 2 Type II report, ISO 27001 certificate, or any other relevant attestations on hand. These are gold because they provide independent validation of your controls.
- Recent Penetration Test Results: Be prepared to share the executive summary from your latest third-party pen test. “Recent” is key here – anything older than 12 months will raise eyebrows. You should also be ready to prove you’ve fixed any high-risk findings.
Having these files neatly organised and instantly accessible means you can respond to initial queries in minutes, not days. That speed makes a fantastic first impression.
Your Essential Due Diligence Documentation Checklist
To make this even easier, I’ve put together a checklist of the core documents most vendors should have prepared. Think of this as your cheat sheet for building a world-class response kit.
| Document Category | Specific Documents & Evidence | Pro Tip |
|---|---|---|
| Security & Compliance | Information Security Policy (ISP), SOC 2 Type II / ISO 27001 certificates, recent penetration test results (summary & remediation evidence). | Keep both the full reports and a customer-friendly executive summary for each. Not everyone needs all the technical detail. |
| Legal & Privacy | Data Processing Agreement (DPA) template, public-facing Privacy Policy, up-to-date Sub-processor List. | Have your DPA pre-approved by your legal team to avoid bottlenecks during contract negotiations. |
| Operational & Technical | Business Continuity & Disaster Recovery (BCDR) Plan, evidence of employee security training, high-level network architecture diagrams. | Anonymise training records to protect employee privacy before sharing. Focus on completion rates and topics covered. |
| Company Information | Company registration details, overview of key personnel, public financial statements (if applicable). | While not strictly security, these documents help build a complete picture of your company’s stability and legitimacy. |
Having these items organised in a central, access-controlled location ensures that anyone on your team can pull the correct, most current version instantly.
Legal and Privacy Documentation
Right alongside security, data privacy is a huge concern for any modern business. Your customers need absolute confidence that you handle their data—and by extension, their own customers’ data—responsibly and in full compliance with regulations like the UK GDPR.
A well-prepared due diligence kit doesn’t just answer questions; it tells a story. It’s the story of a vendor that respects its customers’ risks and has invested in the processes and controls to protect them.
Here are the key legal and privacy documents to include:
- Data Processing Agreement (DPA): Have a standard, pre-approved DPA ready. This document is critical as it defines how you process and protect personal data on their behalf.
- Privacy Policy: This should be your clear, comprehensive, and public-facing policy. Make sure it’s written in plain English, not legalese.
- Sub-processor List: Maintain a current list of all the third-party services you use to process customer data. Transparency is non-negotiable here; hiding sub-processors erodes trust fast.
Operational and Technical Evidence
Finally, you need to provide the tangible proof that backs up all the promises made in your policies. This is where you get into the operational and technical nuts and bolts of how your service actually works and stays resilient.
Be prepared to share materials like:
- Business Continuity and Disaster Recovery (BCDR) Plan: This shows you’ve thought about what happens when things go wrong and have a credible plan to maintain service and recover from a major disruption.
- Employee Security Training Records: You need to prove that your security culture is more than just a policy on a shelf. Evidence of regular security awareness training shows your team is your first line of defence.
- Network Diagrams: A high-level diagram of your system architecture can proactively answer a dozen technical questions in a single image, saving everyone a lot of back-and-forth.
Using a dedicated, shared folder or a purpose-built platform to house all these materials is a game-changer. It empowers your team to deliver accurate, consistent information instantly, turning your vendor due diligence process from a painful bottleneck into a real sales advantage.
What Customers Really Scrutinise During Due Diligence
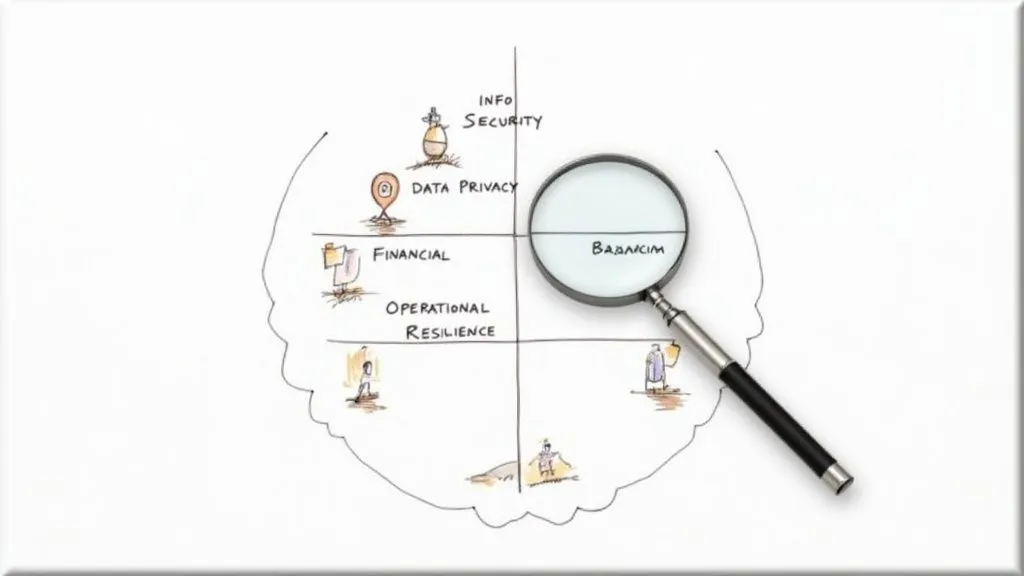
When a customer kicks off the due diligence process, their questions are never random. They’re meticulously probing for potential weak spots across a handful of critical areas in your business. Knowing what these are—and more importantly, why they matter so much—is the secret to giving answers that build genuine confidence, not just tick boxes.
This isn’t about passing a test. It’s about proving you are a reliable, low-risk partner. Your prospective customer is putting their own data, reputation, and operations on the line by choosing to work with you. Their intense scrutiny is a direct reflection of that huge responsibility. By getting ahead of their concerns, you can frame your responses thoughtfully and show you have a mature understanding of their risk landscape.
Information Security and Cybersecurity Posture
This is, without a doubt, the most intense area of questioning for any tech vendor, and for good reason. Customers need absolute certainty that their data is safe in your hands. They’ll dig deep into your security controls, and they want to see hard evidence, not just vague promises.
Be ready for detailed questions about:
- Access Controls: How do you actually manage user permissions? Can you prove you enforce the principle of least privilege across all your systems?
- Data Encryption: What are your specific methods for encrypting data both in transit (as it moves across networks) and at rest (when it’s stored on servers)?
- Incident Response: Where is your documented plan for detecting, containing, and notifying them if a security breach happens?
They’re trying to confirm that your security is baked in, not just bolted on as an afterthought. To really get inside their mindset, it helps to understand the principles of cybersecurity supply chain risk management and see how you fit into their bigger security picture.
Data Privacy and Regulatory Compliance
Data privacy is no longer a legal formality buried in the terms and conditions; it’s a central pillar of vendor due diligence. This is especially true in the UK, where data privacy has become a critical checkpoint. The UK’s Data Protection Act 2018 and UK GDPR place strict obligations on how personal data is handled, meaning your customers will conduct detailed privacy audits to avoid inheriting massive legal liabilities.
If you handle any personal data, understanding your obligations is non-negotiable. Getting familiar with GDPR compliance information is an excellent place to start.
When a customer asks about GDPR, they aren’t just asking if you have a privacy policy. They are really asking, “Can I trust you with my European customers’ data without risking a multi-million-pound fine?”
Financial Health and Operational Resilience
Finally, your customers need to know you’ll still be in business to support them in six months, a year, and beyond. This is where the financial and operational questions come in. They are essentially assessing whether your business is stable enough to be a long-term partner.
This involves looking at:
- Financial Stability: You might not have to share detailed financial statements, but be prepared to offer proof of your viability, like certificates of insurance or details of your funding.
- Business Continuity: What’s your plan for keeping essential functions running during and after a disaster?
- Disaster Recovery: What are the specific technical procedures you have in place to get your systems and data back online after a major incident?
They’re asking a simple question: “If your main office floods or you lose a key data centre, will our service grind to a halt?” Your ability to prove you can weather a storm is just as critical as any security certificate.
How to Actually Answer a Security Questionnaire
That massive, 200-question security questionnaire just landed in your inbox. For a lot of vendors, this is where the sales process grinds to a halt. It doesn’t have to be that way. With a bit of planning, you can turn this dreaded task into a well-oiled machine that actually builds trust with your potential customer.
The secret? Stop treating it like a one-off fire drill and start seeing it as a repeatable process. The first step is simple: who owns this? When a questionnaire comes in, you need a designated point person to quarterback the entire effort. This person isn’t expected to know all the answers, but they are responsible for getting them from the right people.
Assembling Your A-Team for Responses
Let’s be realistic—one person can’t possibly answer everything accurately. Good vendors due diligence is a team sport. You need a small, cross-functional group of experts who can confidently speak to their corner of the business.
Your go-to team will almost always include:
- IT and Security: They’ll handle the deeply technical questions about your infrastructure, access controls, encryption, and what happens when things go wrong.
- Legal and Compliance: These are your experts for anything related to data privacy, regulations like UK GDPR, and the nitty-gritty of contractual obligations.
- Human Resources: They can quickly provide proof of employee background checks, security training programmes, and internal policies.
- Engineering/Product: Who better to explain the nuts and bolts of your service’s architecture and built-in security features?
Once you have your team, map out a clear workflow. It could be as simple as the point person receiving the questionnaire, breaking it down by topic, and assigning sections to the right expert. Whether you use a dedicated platform or a simple, shared spreadsheet, the key is having clear deadlines and owners. This keeps things moving and ensures you’re not scrambling at the last minute.
One of the biggest mistakes I see is one person trying to guess the answers for other departments. Prospects can spot a vague, non-committal answer from a mile away, and it immediately undermines their confidence in you.
Turning a “No” into a Strength
Not every question will be a straightforward “yes.” That’s completely fine. In fact, being honest and transparent about your security posture is far more impressive than pretending you’re perfect. The real skill in the vendors due diligence process is learning how to frame a “no” or “partially” in a way that demonstrates maturity and control.
Imagine a customer asks, “Do you conduct weekly vulnerability scans on all systems?” Maybe your policy is monthly scans for most systems, with more frequent checks on the critical stuff.
- Weak Answer: “No.”
- Strong Answer: “We run comprehensive vulnerability scans across all our production systems every month, a frequency determined by our risk-based security strategy. Our critical, internet-facing assets undergo more frequent, targeted scans. As per our policy, any high-risk findings are fixed within 30 days.”
The second answer doesn’t just say “no”—it gives context, shows you have a thoughtful strategy, and turns a potential red flag into an opportunity. It proves your security programme is mature. For more real-world examples, diving into a good due diligence questionnaire resource can be a goldmine for crafting these kinds of solid, confidence-building answers.
By preparing thoughtful responses like this ahead of time, you slowly build a library of trusted answers that will make every future questionnaire faster and easier to complete.
Turning Due Diligence into a Sales Advantage
Let’s be honest, most people see vendor due diligence as a box-ticking exercise at best, and a sales roadblock at worst. But what if you flipped that on its head? What if it became one of your sharpest tools for closing deals?
A smooth, transparent, and proactive approach to due diligence can be a massive differentiator. It shifts the entire conversation from defence to offence, turning a potential chore into a serious competitive edge.
Picture this: instead of your sales team waiting for a prospect to drop a 200-question spreadsheet on them, they proactively offer a neatly packaged due diligence kit. That single gesture immediately sets you apart from the disorganised competition still scrambling to find their latest policy documents. It shouts maturity, builds instant trust, and can genuinely shorten the sales cycle by nipping security concerns in the bud.
Build a Public-Facing Trust Centre
One of the best ways to get on the front foot is to create a public-facing trust centre. Think of it as a dedicated corner of your website that proves your commitment to security and compliance. It’s your opportunity to tell your security story, on your terms.
A solid trust centre doesn’t have to be complicated. It might include:
- Compliance Badges: Nothing says “we’re serious” like the logos for ISO 27001 or SOC 2. They offer instant visual proof of your hard work.
- High-Level Security Information: You can provide a clear overview of your security programme, data protection measures, and infrastructure without giving away the secret sauce.
- Access to Key Documents: Create a simple workflow for vetted prospects to request access to things like your SOC 2 report or a detailed security whitepaper, usually after signing a quick NDA.
When you make your security posture a visible and accessible part of your brand, due diligence stops being a reactive headache. It becomes a proactive marketing asset that signals to everyone that you’re a secure, reliable partner.
Proving Your Value and Defending Your Price
A well-oiled due diligence machine translates directly into tangible business value. This is particularly true in crowded markets where being seen as the stable, trustworthy option is a massive differentiator. For example, recent analysis of the UK M&A market found that sellers who prepared thorough due diligence reports consistently built more buyer trust and attracted better bids. You can read more about how due diligence impacts UK M&A market trends and see how this principle applies.
When your sales team can talk confidently about security and produce the evidence to back it up in minutes, not days, they aren’t just selling a product. They’re selling peace of mind. That confidence can be the very thing that justifies a premium price tag.
The time and effort you put into organising your documentation and perfecting your response process will pay for itself over and over. Many businesses are now finding that looking into security questionnaire automation is the key to getting the speed and consistency they need.
Ultimately, a polished process shows customers you respect their time and take their risks seriously. And that makes you the obvious choice over a less-prepared competitor.
Answering the Tough Questions in Vendor Due Diligence
Even with a rock-solid preparation plan, vendor due diligence can throw some curveballs. It’s completely normal to hit a few tricky questions, especially when you’re trying to be open with a customer while still protecting your own sensitive information.
Let’s walk through a couple of the most common stumbling blocks I’ve seen vendors run into. Getting your head around these now will help you craft confident, thoughtful answers that keep the deal moving forward.
How Much Information Is Too Much?
This is the big one, isn’t it? A potential customer asks for something like your full, unredacted penetration test report. You know it’s packed with sensitive details about your system’s vulnerabilities. You want to be transparent, but you can’t just hand over a detailed map of your security weak spots.
The trick here is what I call controlled transparency. Instead of sending the entire report, you can provide the executive summary along with a formal attestation of remediation. This shows you’ve done the test and—more importantly—that you’ve actually fixed the serious issues they found.
Here’s how to handle it in practice:
- Share the executive summary. This gives them a high-level view of the test’s scope and major findings without revealing specific, exploitable details.
- Get a remediation letter. Ask the third-party firm that did the test to write a letter confirming that all critical and high-risk findings have been sorted.
- Always use an NDA. Before sharing anything even remotely sensitive, make sure a non-disclosure agreement is signed. This is a non-negotiable layer of legal protection.
This approach builds a huge amount of trust. It proves you’re being upfront while also showing them you have mature processes for handling your own confidential data.
”We Don’t Have That Exact Policy…”
This happens all the time, particularly with smaller, fast-growing companies. A questionnaire lands on your desk asking for your formal, board-approved “Data Classification Policy,” and… you don’t have one. The absolute worst thing you can do is just write “No.” The second-worst thing is to pretend you have it.
Honesty is your best policy here. Your answer needs to pivot to the compensating controls you do have.
Don’t fixate on the document you’re missing; focus on the outcome you’re achieving. The prospect cares less about the title on your policy document and more about whether you’re actually protecting their data.
For instance, a great response would be something like: “While we don’t currently have a standalone ‘Data Classification Policy,’ our data handling procedures are built directly into our Information Security Policy in Section 4.2. These are enforced through our technical controls, and all customer data is classified as ‘Confidential’ by default, with access managed strictly through role-based access controls.”
An answer like this immediately shows you understand the risk they’re asking about and have practical, effective measures in place. It turns a potential red flag into proof that you have a mature, risk-aware culture. This is the kind of practical, honest approach that should define your entire vendors due diligence strategy.