· Jane Iamias · information security policy · 22 min read
What are information security policies? A UK business guide
Learn what are information security policies and why your UK business needs them, plus steps to build a robust cyber resilience framework.

Information security policies are the official, high-level documents that lay out an organisation’s rules for protecting its information, whether it’s digital or physical. Think of them as the constitution for your company’s data, setting clear expectations for employees, contractors, and even the systems you use.
What Exactly Is an Information Security Policy?
Imagine trying to build a secure building without a blueprint. A builder wouldn’t dream of laying bricks without detailed plans, and your organisation shouldn’t handle sensitive data without a clear framework either. This policy isn’t just a list of technical settings; it provides the foundational structure for your entire cyber defence strategy.
It’s a strategic guide that spells out the rules, procedures, and responsibilities for safeguarding your most critical assets—everything from customer data to your own intellectual property. The whole point is to create a consistent, repeatable approach to managing risk.
More Than Just a Document
It’s easy to think of a security policy as just another file that sits on a server to keep auditors happy. But a well-crafted information security policy is a living document. It should guide daily operations and genuinely shape the company culture around security. It’s there to answer critical questions for everyone in the business, from the CEO right down to a new intern.
“An information security policy transforms security from an abstract concept into a concrete set of actions. It clearly defines what is expected, who is responsible, and what happens when rules are broken, making security a shared responsibility.”
This framework gives everyone a single reference point, ensuring the entire team is pulling in the same direction on security. It becomes the source of truth that informs decisions, shapes training programmes, and guides how you respond when things go wrong.
Why This Is Crucial for UK Businesses
Here in the United Kingdom, these policies aren’t just a ‘nice to have’—they’re a business necessity. The need is driven home by some pretty alarming statistics. The Cyber Security Breaches Survey, commissioned by the UK Government, found that 43% of UK businesses suffered a cyber breach in the last year. That figure leaps to 70% for medium-sized firms and a massive 74% for large organisations. It’s worth taking a look at these critical government findings on cyber security breaches to grasp the scale of the threat.
These numbers paint a stark picture of the risk landscape, where a formal policy is your first line of defence. For any UK business, a solid policy is essential for a few key reasons:
- GDPR Compliance: You need to demonstrate due diligence in protecting personal data—it’s a legal requirement under the General Data Protection Regulation.
- Building Client Trust: Customers and partners are far more willing to work with organisations that can prove they take security seriously.
- Operational Resilience: When a security incident happens—and it likely will—having clear guidelines helps your team respond quickly and effectively, minimising disruption and financial loss.
At the end of the day, a strong information security policy is a strategic asset. It protects your reputation, ensures you stay on the right side of the law, and provides the stability needed to operate confidently in a world of ever-present digital threats.
Of course, here is the rewritten section with a more natural, human-expert tone.
Why Your Business Can’t Afford to Ignore Them
So, we know what information security policies are, but why do they really matter? It’s easy to see them as just more paperwork, but that’s a huge mistake. Think of them as strategic assets. A solid set of policies is what separates a calm, controlled response from a full-blown panic when a threat finally hits home.
For any UK business, these policies are the bedrock of everything you do to protect your money, your reputation, and the trust your customers place in you. They shift your entire mindset from being reactive—scrambling to fix things after they break—to being proactive. Instead of a crisis meeting starting with “Right, what do we do now?”, your team can simply open the playbook and get to work. That structured approach is absolutely vital for staying afloat in a sea of ever-present cyber threats.
Safeguarding Against Costly Breaches
At its core, a well-thought-out policy is a shield. It’s designed to protect you from the massive financial and reputational fallout of a data breach. The rules and procedures inside are there to minimise human error, which, let’s be honest, is still one of the biggest weak spots in any organisation’s defences. By setting clear, unambiguous guidelines for everything from creating a password to handling sensitive client data, you dramatically shrink the target for attackers.
Take the classic phishing attack, for example. The UK’s cyber threat landscape shows just how relentless these are. Phishing scams account for a staggering 93% of business-targeted cybercrimes and 95% of those hitting charities. With numbers that high, UK organisations simply must have detailed policies covering staff training, email filtering, and multi-factor authentication. You can dig deeper into the numbers with these UK cybersecurity statistics at ansecurity.com.
Let’s imagine two businesses facing the same attack:
- Company A (No Policy): An employee clicks a malicious link. Chaos erupts. Nobody knows who to tell, there’s no dedicated response team, and there’s certainly no plan to contain the damage. The result? A slow, messy response, far more data gets stolen, and customer trust is shattered.
- Company B (Clear Policy): The same email, the same click. But here, the employee knows exactly what to do. They follow the Incident Response Policy and alert the security contact immediately. The IT team swings into action, isolates the compromised machine, and follows a pre-agreed plan to communicate what’s happened. The damage is contained—quickly and professionally.
Navigating Complex UK Regulations
In the UK, compliance is not a “nice-to-have.” Regulations like the General Data Protection Regulation (GDPR) and the Network and Information Systems (NIS) Regulations place strict legal obligations on businesses to protect data. Your information security policies are the first thing regulators will ask for to prove you’re taking this seriously. They are your evidence of due diligence.
A documented policy shows you’ve actually thought about the risks and put reasonable measures in place to counter them. If a breach does happen, that paperwork can be the difference between a slap-on-the-wrist fine and a penalty that could close your doors for good.
Trying to prove you’re compliant without written policies is an uphill battle. You’re left with no coherent framework to show an auditor, putting your business in a precarious legal and financial position.
Building a Strong Security Culture
At the end of the day, security is a team effort. Policies are the rulebook that gets everyone on the same page, making sure they know their role and how to play it. When your team is trained on clear, easy-to-understand policies, security stops being an annoying extra task and becomes part of the daily routine. This builds a culture of awareness where people feel confident spotting and reporting potential threats.
This cultural shift has another benefit: it makes the business run smoother. When security procedures are standardised, workflows become predictable and consistent. It gets rid of the guesswork, streamlines processes, and lets your team focus on their jobs, knowing there’s a clear and supportive framework keeping them safe.
The Building Blocks of a Powerful Security Policy
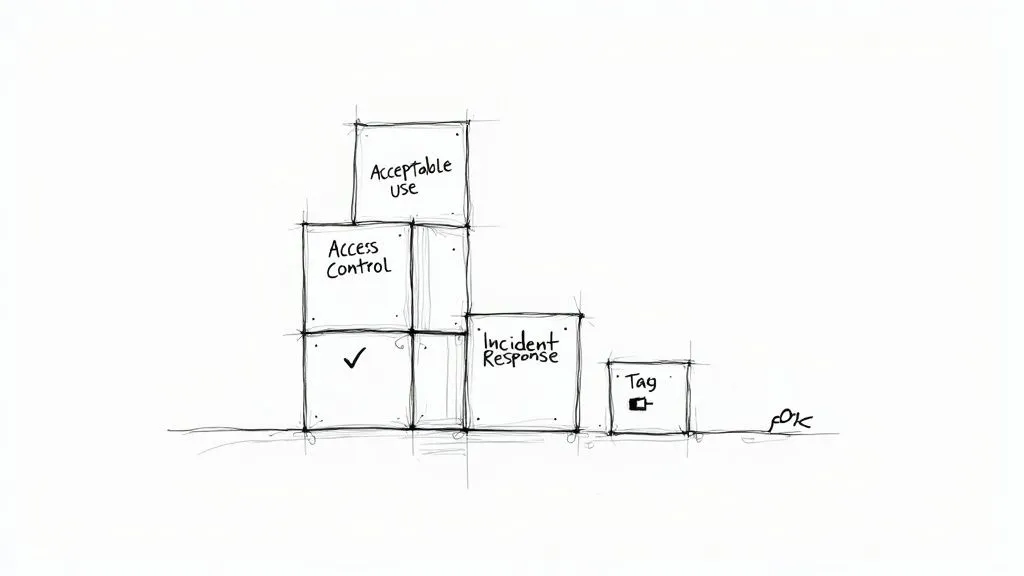
A robust information security policy isn’t some huge, single document you write once and forget. It’s much more like a defensive wall, built from a set of interconnected components that work together. Each “block” handles a specific area of risk, making sure no single vulnerability can bring the whole structure crashing down.
When you break the framework down into these smaller, more focused pieces, the whole task of creating comprehensive security rules becomes much less daunting. Getting to grips with these core components is the first real step toward building a policy that’s not only effective but also easy for your team to understand and follow.
Acceptable Use Policy (AUP)
One of the first and most fundamental blocks is the Acceptable Use Policy (AUP). Think of this as the “terms and conditions” for using company tech. It lays down the ground rules for how employees can use company systems, networks, and data, ensuring everyone is on the same page about their responsibilities.
The main job of an AUP is to stop company assets from being misused, whether that’s browsing dodgy websites on a work laptop or using the corporate network for personal side-hustles. It draws a very clear line in the sand between what’s okay and what’s not, which is a huge help in reducing both human error and potential insider threats.
- Its Purpose: To define clear rules for using company-owned IT assets, like computers, networks, and software.
- A Real-World Example: An AUP might state, “Employees must not install unauthorised software on company devices.” This one simple rule can stop someone from accidentally downloading malware disguised as a handy app, protecting your entire network from a potential disaster.
Access Control Policy
Next up is the Access Control Policy, which is all about the “principle of least privilege”. It’s a simple but powerful idea: people should only have access to the specific data and systems they absolutely need to do their jobs—and not a byte more.
This policy is your first line of defence against both external hackers and nosy insiders. By tightly controlling who can see, change, or delete information, you seriously limit the potential damage if a user’s account ever gets compromised. It’s a real issue, too; a recent study found that nearly two-thirds of companies have over 1,000 inactive user accounts, each one a dusty, forgotten key just waiting for an attacker to find it.
An Access Control Policy works like a digital keycard system. It doesn’t just let people into the building; it ensures each person’s key only opens the specific doors they are authorised to enter, keeping sensitive areas secure.
A solid policy will map out the entire lifecycle of user access—how it’s granted, how it’s regularly reviewed, and how it’s revoked when someone leaves.
Incident Response Plan
Let’s be realistic. No matter how strong your defences are, you have to plan for the day when something goes wrong. The Incident Response (IR) Plan is your step-by-step playbook for exactly what to do when a security incident happens.
The goal here is to enable a fast, organised, and effective response to a breach, like a ransomware attack or a data leak. A well-rehearsed IR plan helps you minimise the damage, slash recovery time and costs, and make sure you meet any legal or regulatory obligations for reporting the breach.
- Its Purpose: To provide a clear, pre-defined set of actions for identifying, containing, eradicating, and recovering from a security incident.
- A Real-World Example: The plan would spell out precisely who to call the second a breach is suspected (like the IT lead and the CEO). It would then trigger immediate actions, such as isolating the affected machines from the network to stop the attack dead in its tracks.
Data Classification Policy
Finally, a Data Classification Policy helps you figure out the value and sensitivity of all the information you hold. Not all data is created equal. Your customer’s financial records obviously need a lot more protection than a marketing brochure you post on your website.
This policy is all about sorting your data into different levels based on how sensitive it is. Once categorised, you can apply the right level of security to each type. It’s a practical approach that makes sure you’re focusing your strongest—and often most expensive—defences where they’ll have the biggest impact.
A typical classification system might look something like this:
- Public: Information that can be shared freely with no risk (e.g., press releases).
- Internal: Data for day-to-day business use that would cause only minor issues if disclosed (e.g., internal team contact lists).
- Confidential: Sensitive information that could cause real harm if it got out (e.g., business plans, employee performance reviews).
- Restricted: Your most sensitive data, often protected by law, which would cause severe damage if compromised (e.g., customer financial details, personal health records).
Real-World Security Policy Examples

Theory is one thing, but seeing security policies in action is where their value really clicks. Let’s look at three practical examples that almost every business needs in today’s world. We won’t just give you boilerplate text; we’ll get into the real-world thinking behind each one.
These examples are all about turning those big, ambitious security goals into clear, everyday rules that your team can actually follow. They tackle common risks that, if ignored, can quickly spiral into serious data breaches.
Remote Working Policy
With hybrid and remote work now standard practice for countless UK businesses, a solid Remote Working Policy is absolutely essential. This document sets the ground rules for how your team connects to company systems from outside the office, shielding your data from the wild west of home networks and public Wi-Fi.
A well-crafted policy should cover a few key areas:
- Secure Wi-Fi: It should be crystal clear that employees must use password-protected, encrypted (WPA2 or better) wireless networks. That means public, unsecured Wi-Fi at the local coffee shop is strictly off-limits for anything work-related.
- Device Management: Any device touching company data—whether it’s a company laptop or a personal phone (BYOD)—needs to be properly secured. This means requiring up-to-date antivirus software, strong passwords, and disk encryption.
Clean Desk and Clear Screen Policy
This one sounds deceptively simple, but its effect on physical security is massive. A Clean Desk and Clear Screen Policy is your first line of defence against someone simply walking by and seeing something they shouldn’t—be it a visitor, a cleaner, or even a curious colleague.
The concept is beautifully straightforward: if you’re not at your desk, sensitive papers should be locked away, and your computer should be locked. This one habit makes “shoulder-surfing” and opportunistic data theft incredibly difficult.
This isn’t just about shuffling paper, either. It’s about building a security-first culture. The policy should mandate that everyone locks their computer (using Ctrl+Alt+Delete on Windows or Cmd+Ctrl+Q on a Mac) every single time they step away, even if it’s just for a minute.
Social Media Policy
Finally, a Social Media Policy is about managing your company’s digital footprint. It draws a clear line in the sand for what employees can and cannot share online, especially when it relates to their work. A single, ill-advised post can accidentally leak confidential project details or cause serious reputational damage.
These policies are a cornerstone of the UK’s cyber resilience, particularly for organisations in high-risk sectors like education and healthcare, which often struggle with long recovery times after phishing or ransomware attacks. Despite having policies in place, NCSC data shows that 67% of medium-sized and 74% of large UK businesses still experience cyberattacks. For a deeper look into this, check out these UK-specific supply chain security requirements.
At its core, this policy is about guiding your team on how to act professionally online, ensuring they don’t give away company secrets, and making it clear when they are speaking for themselves versus for the business.
How to Create and Launch Your Security Policies
Building a solid information security policy framework doesn’t happen overnight, but it’s not an impossible mountain to climb either. Think of it as a clear, manageable journey. This roadmap will walk you through the process, taking you from a blank page to a living, breathing security structure that becomes part of your company’s DNA, not just another document gathering digital dust.
The first step isn’t about writing; it’s about getting everyone on the same page. Before you draft a single word, you need genuine buy-in from the top. Security policies demand resources, enforcement, and a shift in culture, and none of that happens without solid backing from your leadership team. Frame your pitch around business risk, legal duties, and the clear competitive edge that comes from having a strong security posture.
With leadership on board, your next move is to figure out exactly what you’re trying to protect. This means rolling up your sleeves for a thorough risk assessment to pinpoint your most valuable assets and the biggest threats they face. Look at everything – from customer data and intellectual property to the critical systems that keep the lights on. This analysis becomes the bedrock of your policies, making sure you put your energy where it counts the most.
Drafting Your Policies with Proven Frameworks
Once you have a clear picture of your risks, you can start drafting. But here’s a pro tip: don’t start from scratch. It’s far smarter and more efficient to build on the foundations laid by established, globally recognised frameworks. They give you a structured, comprehensive blueprint that has already been battle-tested.
Basing your work on a trusted standard ensures you cover all the crucial security domains and stay aligned with industry best practices. This approach doesn’t just save you a ton of time; it also makes it much easier to prove your compliance to customers and regulators down the line.
Two of the most respected frameworks out there are:
- ISO 27001: This is the international gold standard for managing information security. It provides a complete set of controls for setting up, running, and maintaining an Information Security Management System (ISMS).
- NIST Cybersecurity Framework (CSF): Developed in the US, the CSF offers a flexible, risk-based approach built around five core functions: Identify, Protect, Detect, Respond, and Recover.
Using templates based on these frameworks helps make sure you don’t miss critical details like access control, incident response, or data classification. From there, you can tailor the language to fit your company’s unique operations, culture, and what level of risk you’re comfortable with.
Launching and Embedding the Policies
Getting the policies written is only half the job. The real challenge—and where many companies fall short—is in the launch and getting people to actually follow them. A successful rollout is all about clear communication and great training. Your aim is to make security feel like a shared responsibility, not just another set of rules handed down from on high.
An information security policy that nobody reads or understands is no better than having no policy at all. The launch isn’t just an email announcement; it’s the beginning of an ongoing conversation about security with your entire team.
Organise training that’s genuinely engaging and goes beyond just reading slides. Use real-world examples and scenarios that connect directly to your employees’ day-to-day work. Always explain the “why” behind each policy. When people grasp the real risks a rule is meant to prevent, they are infinitely more likely to get on board.
Your launch plan should cover these bases:
- A Clear Communication Strategy: Announce the new policies through various channels, making sure to highlight how they benefit both the company and every employee.
- Mandatory Training Sessions: Make training a required step for all staff, and build it into the onboarding process for every new hire.
- Accessible Documentation: Make sure all policies are stored in one central, easy-to-find place, like the company intranet.
- Acknowledgement Process: Have every employee formally confirm they have read and understood the key policies. This creates a clear audit trail and reinforces accountability.
Keeping Your Security Policies Relevant and Effective
Getting your information security policies written and signed off is a huge win, but it’s really just the starting line. The world of cyber threats doesn’t sit still, business priorities change, and new tech is always around the corner. Because of this, your policies can’t be static documents left to gather digital dust in a forgotten folder. They need to be living, breathing frameworks that adapt to stay effective.
A policy that was watertight last year could be full of holes today. Think of it like servicing your car—you wouldn’t just drive it for years without a single check-up and expect it to run perfectly and safely. Your security framework needs that same level of consistent attention to protect your organisation against tomorrow’s threats, not just yesterday’s.
Establishing a Regular Review Cycle
The best way to keep your policies sharp is to lock in a regular, non-negotiable review cycle. For most businesses, an annual review is the bare minimum. This formal process forces a scheduled moment to examine every policy for relevance, accuracy, and effectiveness.
This isn’t just about ticking a box for an audit, either. It’s a genuine strategic opportunity to make sure your security measures actually support where the business is heading. During the review, your team should be asking some tough questions:
- Does this policy still make sense for our current business goals?
- Have we brought in any new systems or software that aren’t covered?
- Are there new regulations or compliance standards we now have to meet?
- Has our latest risk assessment uncovered any new threats?
An information security policy is only as strong as its last update. Regular reviews transform policies from historical artefacts into active, powerful tools for risk management, ensuring they provide real-world value.
On top of the scheduled annual check-in, certain events should automatically trigger a policy review. These “event-driven” updates are vital for closing security gaps before they become a real problem.
Triggers for Immediate Policy Updates
Sometimes, waiting a year for the next review is simply too long. A handful of events should ring the alarm bell for an immediate policy update.
- After a Security Incident: A breach or even a near-miss is a painful lesson, but it’s a lesson nonetheless. The findings from your incident analysis should directly inform policy changes to stop the same thing from happening again.
- Adopting New Technology: Rolling out a new cloud service, a CRM platform, or any major internal software fundamentally changes your risk profile. Policies covering things like acceptable use and data handling must be updated to explicitly include these new tools.
- Significant Business Changes: Major shifts like a merger or acquisition, opening a new office, or a big move to remote working all introduce new security challenges. Your policies have to be updated to reflect this new reality.
By building this lifecycle of both regular and event-driven reviews into your process, you create a culture of continuous improvement. Your policies will evolve right alongside your business, making sure your defences are always robust, relevant, and ready to protect what matters most.
Frequently Asked Questions
Even with the best plan in place, it’s natural to have questions when you start putting information security policies into action. I’ve gathered some of the most common queries that come up from business leaders and IT managers to help clear up any confusion and build on the core ideas we’ve covered.
These are straightforward, practical answers designed to help you handle the real-world challenges of building and maintaining a strong security framework.
How Often Should We Review Our Policies?
As a good rule of thumb, you should perform a complete, formal review of all your information security policies at least once a year. Think of this as your annual security MOT.
But that’s just the baseline. Certain events should trigger an immediate review, no matter when your last one was.
- After a security incident: A breach or even a near-miss is a powerful learning moment. Use what you’ve learned to update your policies and stop it from happening again.
- When adopting new technology: Bringing in a new cloud service or a major piece of software changes your risk landscape. Your policies need to adapt to cover these new areas.
- Following significant business changes: Things like mergers, acquisitions, or a big shift to remote working introduce brand-new security challenges that your policies must address.
What Is the Difference Between a Policy and a Procedure?
This is a classic point of confusion, but the distinction is actually quite simple. Imagine you’re planning a road trip. The policy is your destination, while the procedure is the turn-by-turn navigation to get you there.
- A Policy is a high-level statement that sets the rules and goals. For instance, a policy might state, “All sensitive company data must be encrypted when stored.” It’s the ‘what’ and the ‘why’.
- A Procedure is the detailed, step-by-step guide explaining exactly how to follow the policy. For the example above, the procedure would list the specific software to use and the exact steps an employee must take to encrypt a file.
A policy gives you the strategic direction—what needs to be done. A procedure gives your team the tactical instructions—how to do it day-to-day.
How Can Small Businesses Create Effective Policies Without a Big Budget?
You don’t need a huge budget to create solid information security policies. For small businesses, the key is to be practical and focus on high-impact steps, not trying to build a massive enterprise framework overnight.
A great way to start is by using established, free frameworks as your guide. Standards like the NIST Cybersecurity Framework (CSF) provide a brilliant, structured approach for identifying and managing your biggest risks. You can find plenty of templates online based on these frameworks that you can adapt to your own business.
Concentrate on the fundamentals first. Make it a priority to create an Acceptable Use Policy, an Access Control Policy, and a basic Incident Response Plan. Just getting these three in place will make a massive difference to your security posture. The secret is to keep your policies clear, concise, and realistic for your team to follow.
Tired of answering security questionnaires by hand? ResponseHub is an AI-powered platform that automates the whole process, helping your team get through security reviews and close deals much faster. Simply upload your information security policies and other documents to build a knowledge base that can auto-answer up to 90% of questions, complete with perfect, policy-backed citations. Ditch the copy-and-paste grind and see how much time you could save. Explore the platform at https://responsehub.ai.
Article created using Outrank